This page provides an excerpt of Alta’s white paper on 1553 cybersecurity design and test considerations.
Click HERE for the PDF.
For AltaView – Click HERE
For AltaRTVal – Click HERE
Introduction
Cybersecurity refers to the protection of network-connected systems from unauthorized access. Many military and commercial systems have a wide variety of network schemes of interconnected computers that are often an amalgam of new and old protocols/standards. First released in the early 1970s, the MIL-STD-1553 (1553, 1553b) protocol continues to be a widely implemented network for military and commercial systems as it is truly deterministic, fault-tolerant, and time-tested. However, it was not designed to address contemporary cybersecurity issues and could be an entry point for cyber threats. This paper will review aspects of designing and testing 1553 systems with cybersecurity threats in mind.
Intro to Cybersecurity Testing with Alta Products Part I & II – YouTube Videos
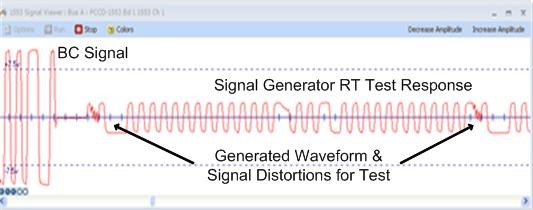
Alta example of injecting distorted signals
Approaches to Resiliency
To implement a complete, robust cybersecurity policy for 1553-based systems, we would ideally revise the protocol to include modern-day capabilities like authentication, encryption, and partitioning. However, this is impractical because it would not address the massive installed base of 1553 systems in operation; nor would it fully address newly designed platforms (F-35 Joint Strike Fighter, for example) that tend to use systems that couple more modern networks (Ethernet, Firewire, Fibre Channel, etc.) with legacy 1553-based systems. MIL-STD-1760, last updated in 2007, is an aircraft-store interconnection spec that includes 1553 as a method of communication and adds a checksum to 1553 messages. It is an improvement over 1553’s word parity only check, but does not provide the protection needed for modern cyber threats.
Instead, increasing the cyber resiliency of legacy embedded systems is a piecewise process of introducing new components to support artificial intelligence/machine learning (AI/ML) algorithms. These algorithms provide anomaly and intrusion detection, logging, warning, and possible mitigation. There are two main approaches, both of which have difficult tradeoffs to manage.
The first approach is to introduce new hardware modules running cyber software applications, either in a distributed or centralized manner, to act as traffic cops for each subsystem. This has enormous impact to system failure rate, failure modes, installation, vehicle weight and maintenance activities. The second approach is to modify the software/hardware of each existing subsystem, thereby making each unit more capable. This too has enormous impact through the ensuing qualification and test activities that need to occur for flight acceptance. Some industry efforts are focused on developing high technology-readiness levels (TRL) for these approaches.
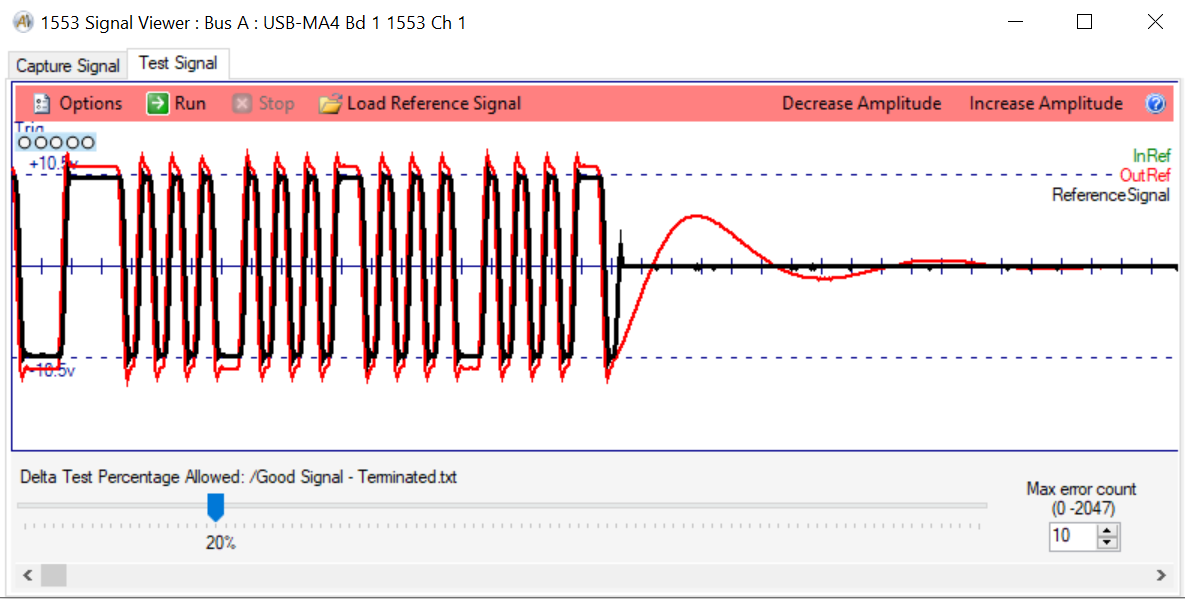
Example of Comparing Signals in an Overlay with AltaView
The Aviation Cyber Initiative, chartered by the U.S. Departments of Defense, Homeland Security and Transportation, has a mission to reduce cybersecurity risks and improve cyber resilience in the aviation ecosystem. A major goal of the charter is to advance cyber research, development, test and evaluation (RDT&E) by enabling collaboration between government and its national labs with private industry and research groups. Funding for cyber efforts is on an upward trend, through Small Business Innovation Research (SBIR) programs and other contract vehicles.
Extensive test and evaluation are required to compile platform data, characterize systems, and develop solutions. Some vulnerabilities are common to all 1553-based systems, and many are unique and application-specific.
This is where Alta Data Technologies can help, with critical tools for development, analysis, simulation, and validation. The armed services and private sector partners rely on Alta’s track record of innovation and quality to advance cyber RDT&E.

